A Story About a Mail, but Not on How to Tell What’s Real
This is a story about an email, about phishing, about AWS Security, and about our current timeline of confusion and rising madness where it is increasingly hard to tell what’s real.
Yep, that’s it, that’s my introduction sentence, you just read it, I’m not taking it back.
But don’t worry I give you some beat to listen to, while we descend into this story. Choose Recommended Beat 1 or Recommended Beat 2.
Pfiatde gets a mail
This story begins, when my friend - redteamer extraordinaire, the bane of Microsoft Teams and probably one of the best to ever do it - Pfiatde (Check out his -> Twitter, and -> Blog) gets a mail regarding an AWS Account.
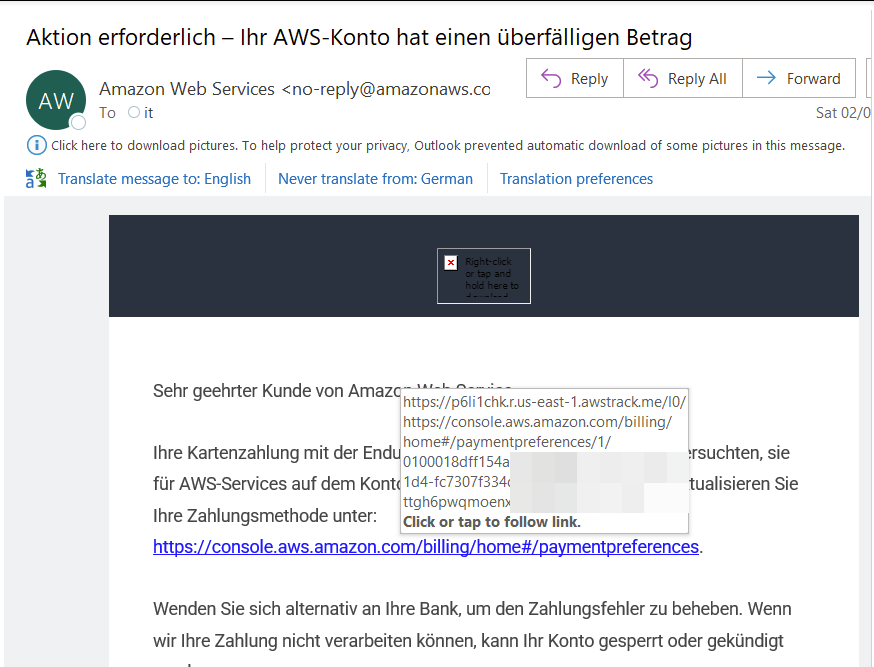
At first glance, this mail seems to be your basic AWS notification mail, directing you to your console login.
However, the URL it wants you to click does not lead directly to the console login, it does instead lead you first to a cryptic link containing awstrack.me.
So, this looks somewhat fishy, but is it?
This means we have now two questions:
- Is this a legitimate email from AWS?
- How would we find out - preferable without clicking the link and providing our login data?
Let’s do a little investigation
We can look at the sender, the link and what the link does.
Starting with the sender, this email seems to originate from no-reply@amazonaws.com. So far so good and one point on the legitness scale.
So, in the email we see “https://console.aws.amazon.com/billing/home#/paymentpreferences", but the actual link is “https://p6li1chk.r.us-east-1.awstrack.me/L0/https:%2F%2Fc........"
Thats not so good, it looks like a different link and a possible redirect and something long and encoded (fishy behavior, minus one on the legitness scale).
Before we click the link, we could google the awstrack.me part.
Well, let’s do it together shall we: click -> THIS
You find stuff like:
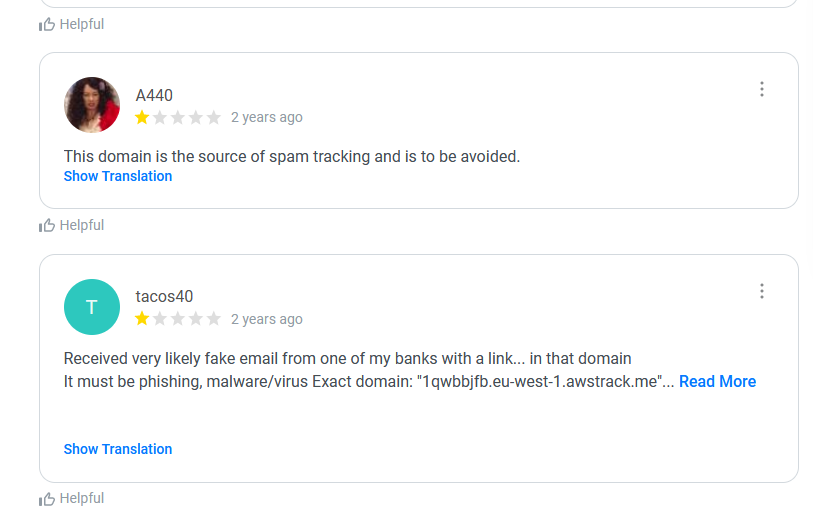
The results are very mixed, between people being convinced its spam, totally legit, phishing, malicious emails and so on. You might also learn it is related to tracking and something about blocks by ad-lists, and firewalls. So, what is it?

So, after googling we don’t really know. Time to check the URL ourselves, where is that hosted?
A quick host should bring clarity, right?
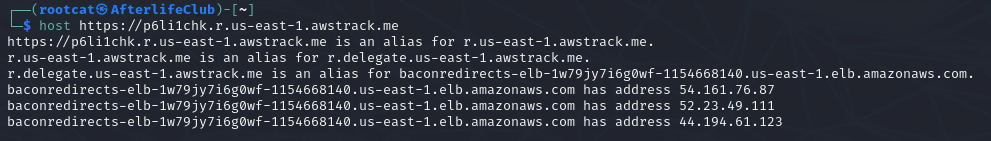
From the us-east-1.elb.amazonaws you know (or at least I do 😉) that these are internet facing load balancers, and If you would check the IPs you would find them to have your usual EC2 whois entries.
Okay this seems weird but looks like it is clearly from AWS.
So, we click the link, with Burp in a VM. Now what happens.
The link click makes a redirect to “https://console.aws.amazon.com/billing/home#/paymentpreferences". Meaning a redirect to the console and directing you to payment preferences after login.
It also makes some posts to “us-east-1.prod.pr.analytics.console.aws.a2z.com” containing some meta-data.
Okay so after the link click this seems legit.
The link itself seemed phishy and our google “research” was also not promising. But by looking at the domain more closely with the host command it was clearly coming from AWS, with AWS IPs load balancers and the like.
So, all is good, nothing to see here. No need to read more of this post choomidos.

The name of the beast
You see AWS uses its own tracking service here, which is used to insert a tracking pixel at the bottom of the email. -> This and -> This
This is the “awstrack.me” part of the link from above.
The mail itself is send by AWS own email service, called SES (-> This) and has something called event publishing which enables you to access the metrics of an email, like was it opened, clicked and so on. -> This
As this is a regional service you get the region in the URL “r.us-west-1”.
This service also allows you to configure where the tracking data is sent, set up domains or DNS zones for it and where to redirect to, after the link has been clicked. -> This
Now at this point you might think:

Same shit different day
Assume someone has gone through the trouble of doing all these steps, in order to send mails with the above-mentioned tracking method and uses AWS email system (SES) for it.
Surely this would be immediately recognizable as being different from the system AWS official email uses. Right? Right?
Let’s make this easy, we start with the one from the potential official AWS mail, with the AWS IPs and load balancers again:

Okay let’s look at another two, this time definitely not from AWS:
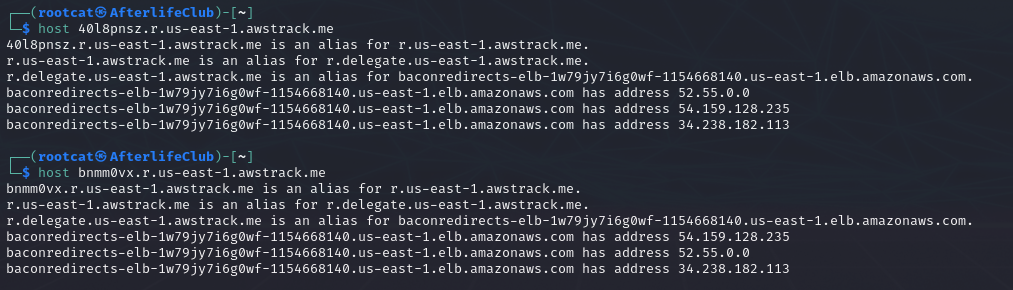
You just get a different random value and then it just depends on your region and the current load balancing setup and yes of all this is inside AWS. Of course, it is, it’s an AWS Service.
Have three more:
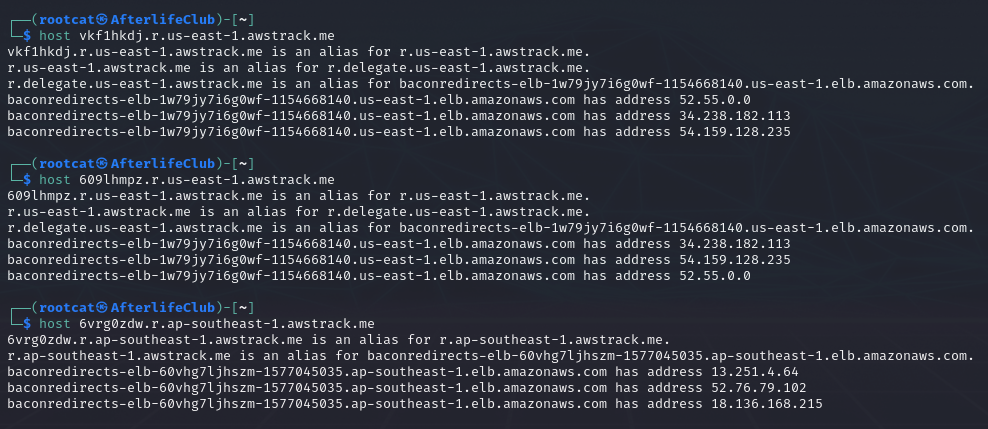
Besides clicking the link, you have no clue on whether this originated from AWS or from a customer using this Service.
The examples you see here, might be one from McDonalds, some from actual phishing and maybe some from myself. I am not actually joking when I tell you, I myself don’t even remember which one was what.
Excuse me, I gotta talk to security now!
Okay so we can actually not tell by the link, not even by looking at it more closely, so how is your typical innocent user supposed to tell what is legit anymore, besides clicking the link and follow through. Time to ask my love-hate buddies from AWS Security (our relationship status is complicated).
So, on the same day Pfiatde got the mail, I wrote to AWS Security and asked them the following two questions from above:
- Is this a legitimate email from AWS?
- How would we find out - preferable without clicking the link and providing our login data?
I also attached them the original email and provided the tracking link.
I got the usual auto reply that they got my mail and are investigating. After about 5 days they send me a notification that they would need more time to investigate this.
Oh, this gonna be good.

After about a week later I got another mail back, I was really excited to open it, what would I learn now, what secret magic and insides into AWS Services would they provide me with?
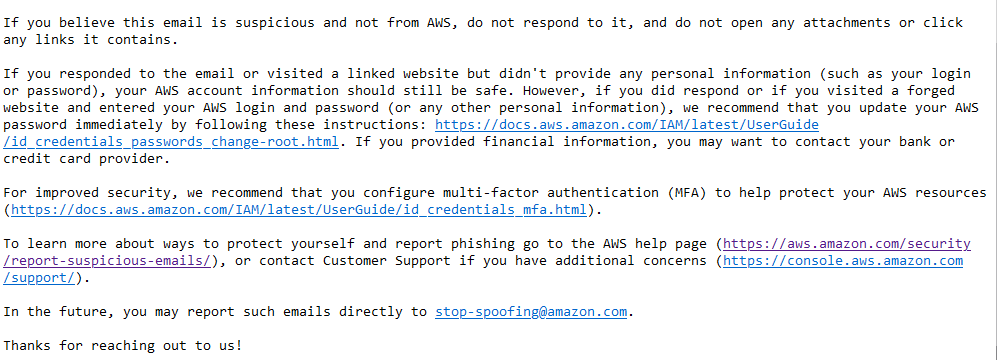
The first sentence is already da bomb!
Let’s read it again:
If you believe this email is suspicious and not from AWS, do not respond to it, and do not open any attachments or click any links it contains.
Friends at AWS Security: -> I AM ASKING YOU IF THIS IS YOUR EMAIL! <-
So, after more than a week of “investigating” AWS cannot tell me if this is their mail. Brilliant. What more do you want? Are we not entertained?

Okay breathe little buddy, what about the “report suspicious email” part they talk about, maybe they know more.
Jap, I tried that next. In total I tried with them and AWS Security for a total of 7 Weeks.
To this day I have no answer on this issue whatsoever never mind my posed questions. I got nothing more from security and from the suspicious email team I never got a single response. Just nothing. They ghosted this cat entirely.

So was this fake or not, tell me!!!
I believe the mail that Pfiatde got from AWS was a legitimate mail from AWS using their own tracking service. I base these claims not on the link, but on me actually clicking it and going through while looking at what it actually does, however you have to take my word for it, cause AWS definitely would or could not confirm or deny their own mail.
So, what to make of this. Well, with the use of cloud thingies and let’s say not so smart choices of big organizations it gets increasingly hard to see what something is and where it comes from, never mind from whom.
It also means you can send out mails using AWS resources for all sorts of phishing scenarios and have a pretty good tracking with it (assume someone is already doing that), although the initial setup is a little tedious.
I thought about making a full setup for it, with auto deploy scripts and all of it, but to be completely truthful, clicking it together works fine and if you just follow already existing setup SES tutorials the knowledge is already out there, plus I couldn’t be really bothered with it, I must finally finish the last act of Baldur’s Gate 3.
I also believe to some degree AWS is aware of this, if this is why they never gave me any kind of answer or if this is just pure incompetence, well your guess is as good as mine.