When Elon doubled your Bitcoin - Cyberthrowback Twitter-Hack
In July 2020, Elon Musk was probably wearing his spending pants, tweeting to his then 30 million or so followers:
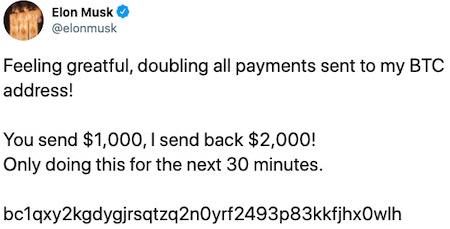
And Musk wasn’t alone in his generous offer to double his followers’ Bitcoins for charity; Bill Gates, Warren Buffet and many other celebrities also posted similar tweets. A total of 130 - including 45 prominent and high-reach - Twitter accounts became part of the scam, because of course this was not a generous offer from the rich and powerful, to give us a little money.
How did this account theft go down and who was responsible for it? This and more is clarified in this post about the Twitter Bitcoin scam.
From LinkedIn to Admin
Graham Ivan Clark along with two fellows (apparently Mason Sheppard and Nima Fazeli) used paid tools to search LinkedIn for Twitter employee contact information. These tools, sometimes called scrapers are used by totally annoying tech-recruiters, are powerful tools to extract data, such as email addresses, phone numbers, job titles, and connections of a company. As arstechnica reported, they focused on employees who were likely to have higher or administrative privileges. In the next step, the hackers created web logins that mimicked Twitter VPN logins and acted as fake VPN login portals into the internal Twitter network.
Using the collected information and their fake login page (evil twin) to the internal network, the attackers contacted Twitter employees who were currently in their home offices due to the pandemic situation. They impersonated Twitter employees and tricked their victims into entering their credentials on the fake login page. But what about MFA? Well, when the credentials were entered in the fake page, the hackers entered them in the real one, trigging the MFA prompt. The victims would then enter their two-factor authentication, and the hackers could log in to the real VPN login with the stolen data. This is why MFA does not necessarily protect against phishing as some orgs would often like to believe.
The fact that it is comparatively easy to gain access to internal tools, and that once this has been achieved, no meaningful additional checks take place, was probably something Twitter itself had been aware of for some time. However, it has decided against changing this practice. Quote bloomberg:
Former members of Twitter’s security departments stated that since 2015, the company was alerted to the potential from an inside attack, and other cybersecurity measures, but these were put aside, in favor of more revenue-generating initiatives.
According to Mudge, this was as bad as it sounds, the Guardian quotes his statement, before congress: “It’s not an exaggeration that any employee could take over the accounts of any senator in this room,” he said.
After the incident, Twitter claimed to have both changed this practice and explicitly trained employees on social engineering resiliance, as is often the case, after it was, of course, too late.
Clark and his comrades-in-arms, however, could not rejoice for too long about their successful action and the appproximatly 100,000 dollar they had earned with the scam. Not even two weeks after the incident and the prominent tweets, all three were identified and charges were filed against them.
No OPSEC, no cookies!
To avoid getting caught as a criminal hacker, it is essential to leave no relevant traces or information behind. This typically requires a complex network of VPNs, proxies, compromised systems and fake identities in combination with robust and encrypted proprietary systems. On the scene, this is known as operational security, or OPSEC for short. Graham Clark and his buddies seemed never to have heard of it.
As can be seen from some articles (wired) and especially from the court documents, the three defendants made it espcially easy for the investigators. In principle, such investigations are often divided into several parts including a technical attribution and an intensive investigation about the money flow (follow the money). From a technical point of view, it was quickly clear where to look for the people behind this scam, because exactly on the day of the hack, hacked Twitter accounts were offered for sale in the OGusers forum. The forum in question is very social media-oriented and is frequented by a younger audience. Moreover, it is rather ridiculed in the scene, as it has been hacked several times in the last few years. In fact, this happens so often that the administrators simply copied their reports that a hack had occurred and all the data had been leaked from previous cases and exchanged the date. Nowadays, there are often not even any announcements any more, and the users then find out about it from other forums.
The investigators used such a leak to look up the entire chat history of the Twitter account providers from the OGusers forum and connect it to real people. This was easy, as one of the attackers actually used his private email address (with first and last name) to log into the forum. Yes, really.
When investigating the Bitcoin addresses or following the money trail, the investigators found that these wallets were not only hosted at coinbase, one of the largest providers in this field, but also that they had been used for smaller scams before. Thus, even a short request to the crypto trading platform was enough to obtain the data of the owners of the wallet. This immediately led to the defendants, as they had not set up any fake identities. One of the responsible parties had even uploaded his driver’s license for verification purposes.
This makes the extremely fast success of the investigation completely understandable. However, one small detail remains: In the chats on OGusers, another person was involved, but this person had adhered to at least minimal OPSEC and could therefore not be identified. However, the investigators are sure that the convicted Clark was the head of the gang, so the case is considered closed with his confession, as far as they are concerned.
Make Zoombombing great again
However, persistent rumors and conspiracy theories regarding this hack were circulating in the hacker scene for a while. On the one hand, the attackers were able to compromise the Twitter platform using only LinkedIn information and control the accounts of the most powerful people in the world for a short period of time, which was then only used for a comparatively simple scam, but on the other hand, they did not take any measures to conceal their own identity. This discrepancy between the obvious skill of the accused and the simultaneous lack of OPSEC (make that zero) made some in hacker circles doubt the “official” version of the story.
From another direction, there were even brief suspicions that the Trump camp was behind the action, as the account of the then US president was suspiciously not taken over. However, it turned out relatively quickly that this was simply because Trump’s Twitter account had an elevated protection status and could not be taken over using Twitter’s internal tools.
However, as more became known about the actors and also their previous machinations, the debate on the web tended to shift to the fact that the whole affair had gone extraordinarily smoothly for Twitter, since “only” Bitcoin scammers and not professional groups had hacked the platform and celebrity accounts. After all, a tweet from Elon Musk or Warren Buffet can influence stock prices, and Joe Biden’s account could potentially trigger diplomatic crises. Twitter would probably agree with this assessment.
It got funny again when it came to the hearing of Clark, which took place via Zoom in a meeting without waiting room control and password protection. Of course, the virtual hearing was then immediadly infiltrated by trolls and had to be interrupted after a screen broadcast of several porn clips (For those who like to watch: here). The quote from a Twitter user almost aptly sums up the proceedings: Did no one involved have an 18-year-old that could teach them how to do this securely?
All in all, the case described here reveals that a group of young people has succeeded in screwing one of the largest social media corporations in the world. On the one hand, this proves how neglected the defense against phishing and social engineering attacks is, even at the largest companies in the industry. Combined with an overall really bad internal security architecture. On the other hand, it also proves how effective these attacks can be. The fact that there was nevertheless an investigative success and conviction of the perpetrators can be attributed to their lack of professionalism and complete abandonment of OPSEC measures. Overall this whole story could have been a lot worse for Twitter if the usual teenagers behind the attack, would really have been a professional group with other targets in mind than a bitcoin scam.